Escaping
In many experiments participant inputs are displayed to their partners. Although the data should have been validated before, an information output should always be escaped. This means that every input will be shown as plain text, instead of potentially interpreted code. The reason for this approach is code that might eventually be harmful. Participants could enter code instead of number inputs and try to access your database or utilize the server performance to full capacity.
Below you see an example, where escaping is used. The php function htmlentities escapes every potentially harmful code and converts it to HTML entities.
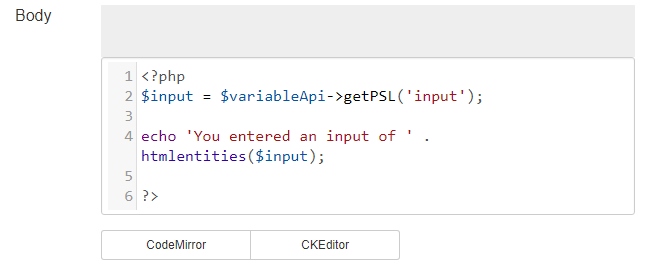
The output of the code is displayed here. It shows the entered input and ignores any functionality of the script tags. In case you are not sure, whether to use escaping or not, you should use it.
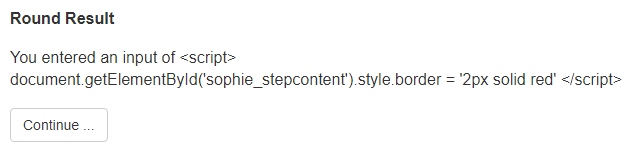
To give you an example of how the same code looks without escaping have a look at the next screenshot.
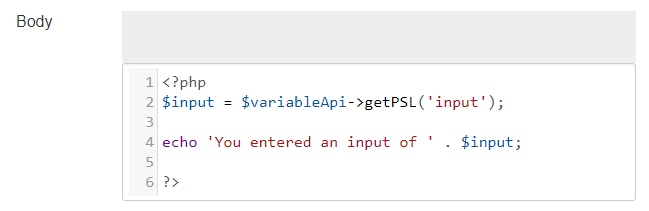
The exact same code without the htmlentities function leads to a totally different result. The JavaScript code is executed and for this example the border of the step content is changed. More harmful than minor changes to your CSS might be ajax requests, that utilize 100% of your server performance, as this prevents the other participants from proceeding.
